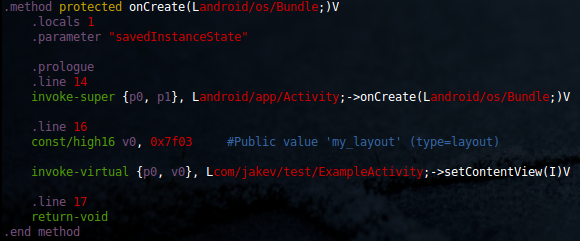
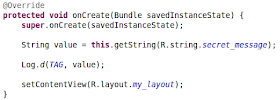
I'm finally happy to say that the beta for my ongoing project called "CobraDroid" is fully released! The project was actually released back in March on my website, but the source was just pushed to GitHub recently. I wanted to talk a little about what CobraDroid is, what it can do for analysts, and what you can expect in the upcoming months.
What Can CobraDroid 1.0 Beta Do?
CobraDroid is a modified Android emulator image designed for individuals who want to perform application security assessments or analyze malware for the Android platform. It is not a service where you upload an application and receive a summary of activity, and it is not a black-box (there are plenty of those out there). It should help you with performing your analysis, but keep in mind it will not perform all the analysis for you. It is released under the Apache Software License 2.0, so you are free to download, modify, and use the source. The beta is mostly a teaser for what is to come, but it includes:
- Configurable radio values (MIED, MDN, IMSI, SIM card serial number, and voicemail number)
- Dynamically configurable “build.prop” values
- Configurable SSL certificate validation bypassing
- Enhanced proxy capabilities
- Additional user-space utilities
This should be enough to get you started, and already provides more functionality than the standard Android emulator.
What's Next?
The beta version of CobraDroid 1.0 is still lacking in terms of functionality and features. Luckily, I've been hard at work on lots of new features. I don't want to give away all the fun, but from a high level you can expect 1.0 to include:
- A newer, hand-ported kernel (say goodbye to the 2.6.29 Goldfish kernel)
- Full Bash shell + Busybox
- Application specific packet-capturing
- Java bytecode instrumentation
- Mercury and LiME integration
- ..and more!
Many of these features are actually already implemented, but in a state of QA. CobraDroid 1.0 should be ready to roll by the end of the summer, so stay tuned!
BruCON 2013
If by chance you are attending BruCON 2013, come check out my talk on CobraDroid and see a demo of the tool! Hopefully I'll be presenting the tool in the states soon as well sometime soon.
If you are interested in trying CobraDroid, check out the getting started page. Of course, feedback and comments are always welcome.
-jakev
If you are interested in trying CobraDroid, check out the getting started page. Of course, feedback and comments are always welcome.
-jakev